There’s a funny catch-22 when it comes to privacy best practices. The very techniques that experts recommend to protect your privacy from government and commercial tracking could be at odds with the antiquated, vague Computer Fraud and Abuse Act (CFAA).
A number of researchers (including me) recently joined an amicus brief (filed by Stanford’s Center for Internet and Society in the “Weev” case), arguing how security and privacy researchers are put at risk by this law.
However, I’d also like to make the case here that the CFAA is bad privacy policy for consumers, too. [Read more…]
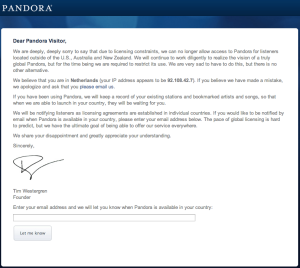
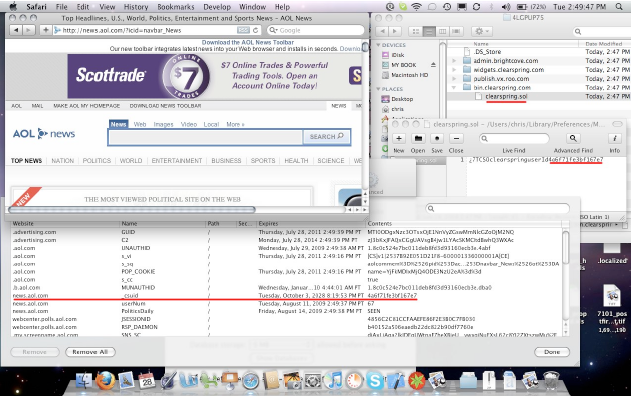
 I thought I’d take the time to elaborate a bit further regarding the technical mechanisms described in our
I thought I’d take the time to elaborate a bit further regarding the technical mechanisms described in our