I research the way private companies and the government take advantage of the digital trail individuals leave behind. This part of my work raises questions on what accountability and transparency measures we should expect from our government and private companies.
Tech and Security Consultant for the Washington Post
From September 2013 to October 2014, I worked as a technical expert and security advisor at the Washington Post. You can read a full portfolio of my articles and contributions here, but here are a few highlights:
| NSA tracking cellphone locations worldwide, Snowden documents show The NSA uses massive numbers of cell location records to determine if anyone, including US citizens, are co-traveling with targets of surveillance. Read more. | |
 |
NSA infiltrates links to Yahoo, Google data centers worldwide, Snowden documents say The NSA taps into the private lines of connecting the data centers of email providers like Gmail, scooping up American’s information in the process. Read more. |
 |
NSA collects millions of e-mail address books globally The NSA is collecting address books and buddy lists of American users as the data is transmitted around the globe. Read more. |
Independent Research and Comments on the National Security Agency
The documents leaked by Edward Snowden had a profound impact on how we understand the capacity of the government’s surveillance capabilities. My work focuses on understanding and describing the technical nature and details of these programs. I have released several comments arguing that it is necessary to have a technical expert advising those tasked with keeping this system in check.
 |
Tiny Constables and the Cost of Surveillance: Making Cents Out of United States v. Jones The Yale Law Journal Online (YLJO) published an article that I co-authored with Kevin Bankston in which we show how technology has drastically reduced the barriers to conducting location surveillance. We estimate the hourly cost of location tracking techniques used in landmark Supreme Court cases Jones, Karo, and Knotts and use the opinions issued in those cases to propose an objective metric: if the cost of the surveillance using the new technique is an order of magnitude (ten times) less than the cost of the surveillance without using the new technique, then the new technique violates a reasonable expectation of privacy. Read the full article here. |
 |
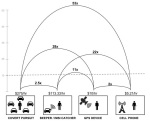
Infographic on How PRISM May Work I created this infographic using publicly available documents and official statements. It provides a description of what the PRISM surveillance program might look like from a technical perspective. Read more |
 |
Comments to the Privacy and Civil Liberties Oversight Board I joined a panel of technologists to describe what oversight and transparency measures we would like to see installed in the NSA surveillance programs. I submitted official comments describing my concerns and reocmmendations to the Federal Register on July 31, 2013 My comments focused on asking the NSA to release metadata on the extent of their data collection. Read more |
 |
Comments to the Review Group on Intelligence and Communications Technologies I joined a group of technologists to submit comments on the need for a technical expert to advise this panel. Our comments include a number of technical questions that we feel this panel should ask of the intelligence community and, when possible, make the answers publicly available. Read more |
Wall Street Journal’s “What They Know” Series
As part of their What They Know series, the Wall Street Journal published a number of articles about the ever-expanding use of technologies to track, watch, and conduct surveillance on the public. I served as a technical consultant on the following articles:
 |
Surveillance Catalog I worked with the Wall Street Journal on a pulitzer finalist package taking a deep look at the surveillance technology trade. Story and interactive features available here. |
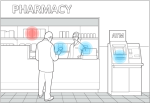 |
The Surveillance Economy The Wall Street Journal cataloged more than 20 different ways information about people can be recorded during everyday activities, from license plate readers, to DVRs, to medication purchases at your pharmacy. Read more |
 |
U.S. Firm Acknowledges Syria Uses Its Gear to Block Web Blue Coat Systems, a U.S. company that makes Internet-blocking gear acknowledges that Syria has been using at least 13 of its devices to censor Web activity there—an admission that comes as the Syrian government cracks down on its citizens and silences their online activities. Blue Coat Systems says it shipped the Internet “filtering” devices to Dubai late last year, believing they were destined for a department of the Iraqi government. However, the devices—which can block websites or record when people visit them—made their way to Syria, a country subject to strict U.S. trade embargoes. Read more |
Research and Talks
 |
In August 2012, I was a guest on the Kojo Nnamdi discussing facial recognition software and other surveillance issues. |
 |
I worked with Kevin Bankston to provide data on the decreasing cost to the government of surveilling its citizens. We looked at the hourly cost of various methods of location surveillance to provide a mathematical foundation for a discussion on fourth amendment rights. |

