I wrote this essay for a conference hosted by PEN America on the chilling effects of surveillance. I was asked to address what questions researchers should focus on and I discussed the threat posed by stored data and the opportunity for researchers to create new transparency tools. It was originally published here, but you can also read it below!
How do we protect something we can barely see?
As much time as we spend discussing privacy, you would think it’d be easy to define. Yet the more we discuss it, the more it becomes apparent that our definitions of privacy vary widely. For some it means keeping only their deepest secrets safe, while for others any information collected about them without their consent is perceived as a violation. Despite these inconsistencies, most definitions of privacy depend on knowing and controlling what information is collected about us.
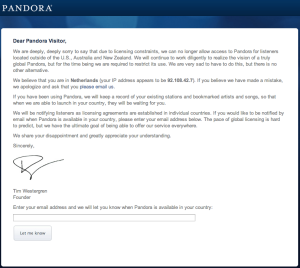
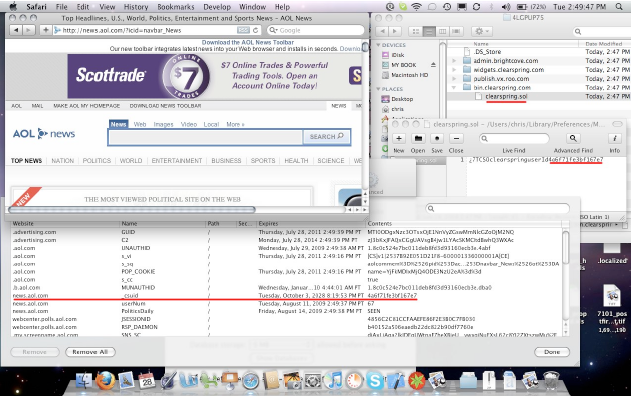
Most of the time users don’t realize how much information they are sharing, how it’s stored, or who has access to it. In the analog world, controlling one’s own information was relatively straightforward. Obvious physical and cost barriers limit how quickly and how far information about an individual can be shared. Its reach was our personal circle of friends or maybe a wider community if there were a diligent town gossip. But technology has expanded the reach of information significantly. Now, there are vast quantities of data collected about individual users daily, often stored indefinitely in data centers operated by private companies, and available to anyone that is granted (or can forcefully obtain) access. [Read more…]